Muddled Libra Threat Group Targets SaaS and Cloud Platforms for Data Discovery and Exfiltration, Write-up Shared on X
Threat Analysis
On April 9, 2024, a report from Palo Alto Networks’ Unit 42, @Unit42_Intel on Twitter, revealed updated tactics, techniques, and procedures (TTPs) used by Muddled Libra, a group driven by financial gains. During the period from late 2023 to January 2024, Unit 42 tracked Muddled Libra exploiting Software-as-a-Service (SaaS) platforms for reconnaissance and using Cloud Service Provider (CSP) frameworks for data theft. SaaS platforms help businesses improve efficiency, scale dynamically, and support telecommuting, whereas CSPs like Amazon Web Services (AWS) and Azure provide infrastructure management, software updates, and disaster recovery services.
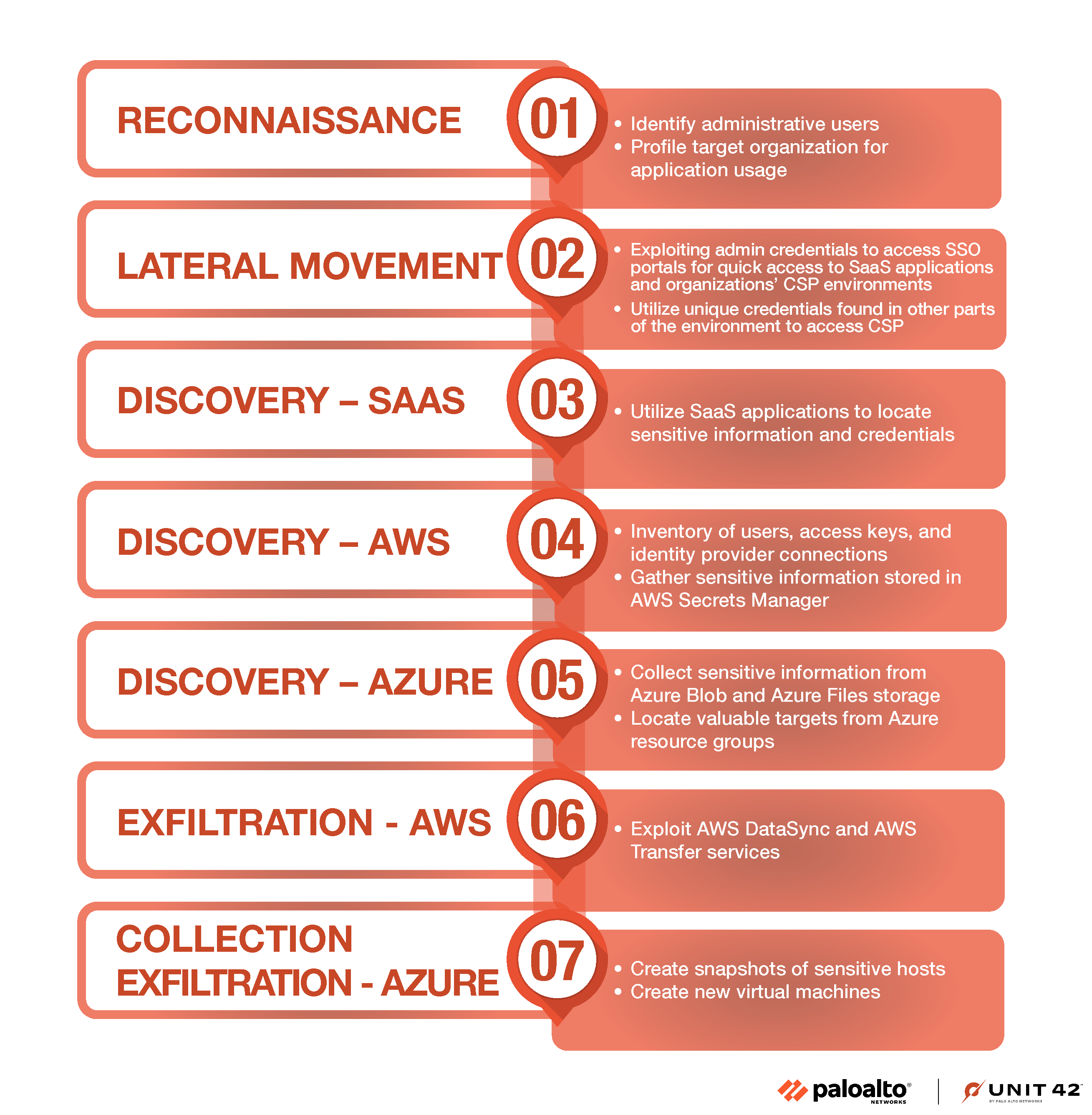
Unit 42 outlined the phases of Muddled Libra’s recent activities as follows:
Initiated social engineering schemes to acquire administrative credentials within an organization, subsequently leveraging these to widen their footprint across the organization’s SaaS and CSP solutions via identity and access management (IAM) exploitation.
Utilized these credentials to log into single sign-on (SSO) gateways, granting them entry to various organizational SaaS tools.
Breached the entity’s SSO system to infiltrate its cloud platform, actively searching for unprotected CSP credentials within the internal network.
Harvested sensitive information from within SaaS platforms, including user credentials and system configurations, to map out the organizational infrastructure.
Penetrated the organization’s cloud framework to extract details on user roles, security keys, and confidential data across different cloud services.
Misused CSP functionalities, like AWS DataSync, AWS Transfer, and Azure snapshots, for data exfiltration.
Unit 42 emphasized the complexity of defending against Muddled Libra’s refined strategies in data acquisition and removal, highlighting the advanced techniques the group uses to exploit cloud and SaaS environments.
Kill Chain Reference by Unit42
References
https://unit42.paloaltonetworks.com/muddled-libra-evolution-to-cloud/

