Threat Actor "232" Re-Sells 795,495,961 Records of ICMR Data Breach
Table of contents
Threat Summary
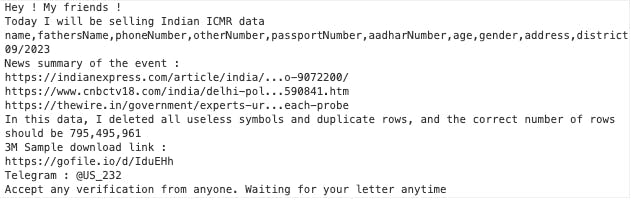
On April 21, 2024, a threat actor with the username "232" on BreachForums has uploaded a post indicating the sale of ICMR data breach database. The data breach contains different PII parameters such as "Name", "Father Name", "Phone Number", "Other Number", "Passport Number", "Aadhar Number", "Age", "Gender", "Address", and "District".
The threat actor further provided references to the news article references from Indian Express, CNBC TV and the Wire which covered the ICMR data breach incident. Based on my understanding, this sale could potentially be a re-sale of the previous ICMR data breach.
The threat actor claimed to delete all unnecessary symbols and duplicated rows from the download of compromised database.
To quote, "In this data, I deleted all useless symbols and duplicate rows, and the correct number of rows should be 795,495,961"
The threat actor further shared a 3 Million sample that can be downloaded from gofile.
The Telegram ID of the threat actor is: @US_232
Sample Download Link: gofile.io/d/IduEhh (Please maintain caution while browsing this link as it is not verified/validated and could have malware embedded in it)
The sample has been made available for download. Responsible individuals can validate the same at their own authority.
Evidence
References
BreachForums - https://breachforums.st/Thread-SELLING-ICMR-Indian-815M-data-Breach-Streamlining-795-495-961?action=lastpost

